No Risk, No Fun? Beware Of Careless Use Of MCP
Vibe coding has arrived at Go. With a single prompt, you can create a complete CLI tool like this #definitelynotbiased Go tool for detecting Rust in Linux systems.
If you are a real vibe coder, you won't be satisfied with simple single-prompt tools, though. The real magic comes with MCP, the Model Context Protocol that puts truckloads of powerful tools to an LLM's fingertips. (Provided that the LLM has fingertips, or, in other words, is tools-aware.)
In case you haven't tried a tool like Goose, Claude Code, Cline, Continue, or any other MCP-aware platform, try it! It's fun, believe me. I tried it too, and it's fascinating to see how an algorithm based on statistic models and a few matrix calculations goes ahead and churns out code for you.
Ok, did you try it now? And it was fun, right? Great, because I'm here to spoil the fun.
How MCP works
The Model Context Protocol describes a client-server architecture with an “agentic app” at the center. An agentic app connects to LLMs and MCP servers. An MCP server exposes a tool, such as a web search, file access, or some remote service, to the agentic app. The app, in turn, can tell the LLM, “here is a tool that you can use.” The Model Context Protocol ensures that the LLM knows what a tool does, how to invoke it, and how to read the results.
Here is a diagram of the MCP architecture:
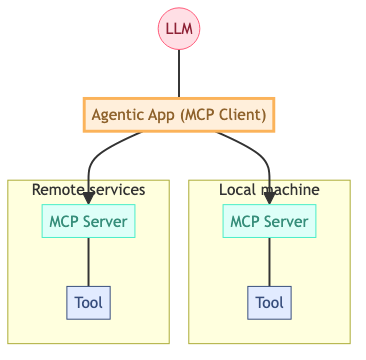
The architecture looks simple enough; what could possibly go wrong?
How an agentic app is vulnerable to attacks and misbehavior
The idea of an agentic app is to give an LLM control over tools to examine and manipulate external instances: your local file system, databases, services that you are connected to, and more. Here are some pitfalls to avoid:
Unrestricted access: By default, agentic systems start in “Ask” mode, where the user has to approve every request for using a tool. Getting constantly asked for permission can become tedious, which is why many users switch to auto approval mode, letting the LLM invoke tools as it needs.
But even in “Ask” mode, you cannot be sure what specific series of tasks the LLM runs. The LLM doesn't even need to hallucinate in order to wipe out files that you'd rather keep, or wreak havoc in some other way.
Precautionary measure: Always have a backup, and if the LLM requests to use a tool, ensure that it tells you what exactly it wants to do.
Unauthenticated MCP servers or tools: The MCP specification lists authorization as optional. Adding an MCP server to an agentic app is as easy as adding a few lines of JSON to the agent's config. An attacker could replace the MCP server or tool without you noticing.
Precautionary measure: Use only tools with authentication, or at least know the tools you expose to your agentic app. If it's open source, take some time to inspect it or let an LLM check the code for malicious intents or vulnerabilities.
Malicious MCP servers or tools: The MCP servers or tools can act in malicious ways, especially if they are remote services. For example, an MCP server or a tool could try to inject malicious prompts to make the LLM gather and leak sensitive data.
Precautionary measure: Examine each new MCP server or tool that you intend to use for trustworthiness.
Compromised MCP servers: MCP servers may store credentials for the services they connect to, such as your mail account or your GitHub organization. Attackers who gain access to these credentials can pull sensitive data or abuse the service.
Precautionary measure: Shield your MCP servers as good as possible from outside attacks. When connecting to remote MCP servers outside your control, you might even want to consider not using this server at all.
This is only a fraction of possible attacks and misbehaviors, but it should be enough to get the point across; for more details, find further reading here, here, and here.
To be clear, I am not trying to say, “all MCP is evil”. With sufficient caution and common sense applied, doing some Go coding with an AI buddy can be fun and—maybe—insightful.
